Category: Forensics
Points: 100
Description
The low-effort wave 🌊 Ride the wave man. 🏄♂️🏄♀️🌊
The wave is life. The waves are like, sound, and like water, and like cool and refreshing dude.
But waves are hard to ride. So listen to them instead, crashing on the seashore. Listen to the music of the sea. Like the theme this year is music or something. So I theme this challenge, like, minimum effort music. Listen to this attached .wav file. It’s amazing. Or so I’ve heard. Or rather, haven’t. Something’s broken with it. I don’t know dude.
It also doesn’t work. Can you fix this for me? I think there’s a flag if you can find it.
Wav file: low effort
First step is to try and play the wav file. When we try, we see that it cannot be played. Usually my first step is to either run file filename.wav to see what we are working with or to open the file in a hex editor (I use the one provided in vscode). Opening in a hex editor we see that the magic numbers (file signature) is PNG.
We can then change the file extension from .wav to .png. Now if we try and open the file we see an image of a discord conversation.
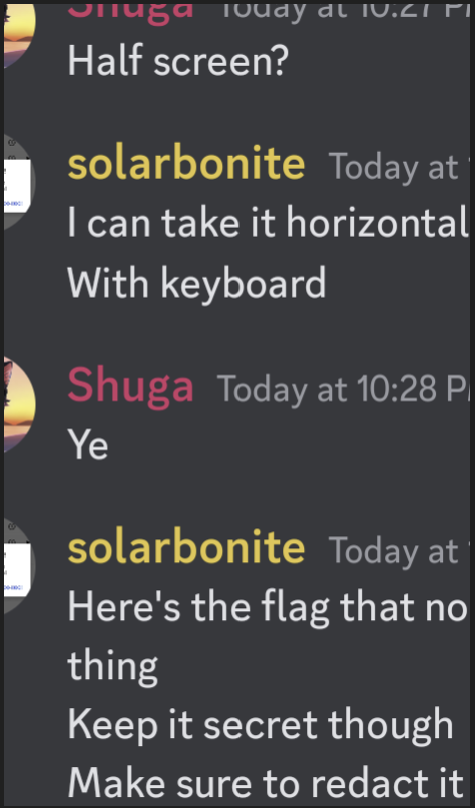
I have solved a similar challenge and recognized that this is an aCropalypse exploit for android devices where a screenshot that has been edited (using android’s markup tools) can be reconstructed. All we need to know is the type of phone that this screenshot is from and then we can put it into the online tool acropalypse.app. To find the phone model we can either run exiftool filename or strings filename. Exiftool will usually be more helpful but for this challenge both work.
exiftool low_effort.png
Unique Camera Model : Google Pixel 7
strings low_effort.png
<?xpacket end='r'?>
jeXIfMM
Google Pixel 7
IDATxBoth tell us that the mode is a Pixel 7 which we can enter into the tool and it will return an image containing the missing parts.
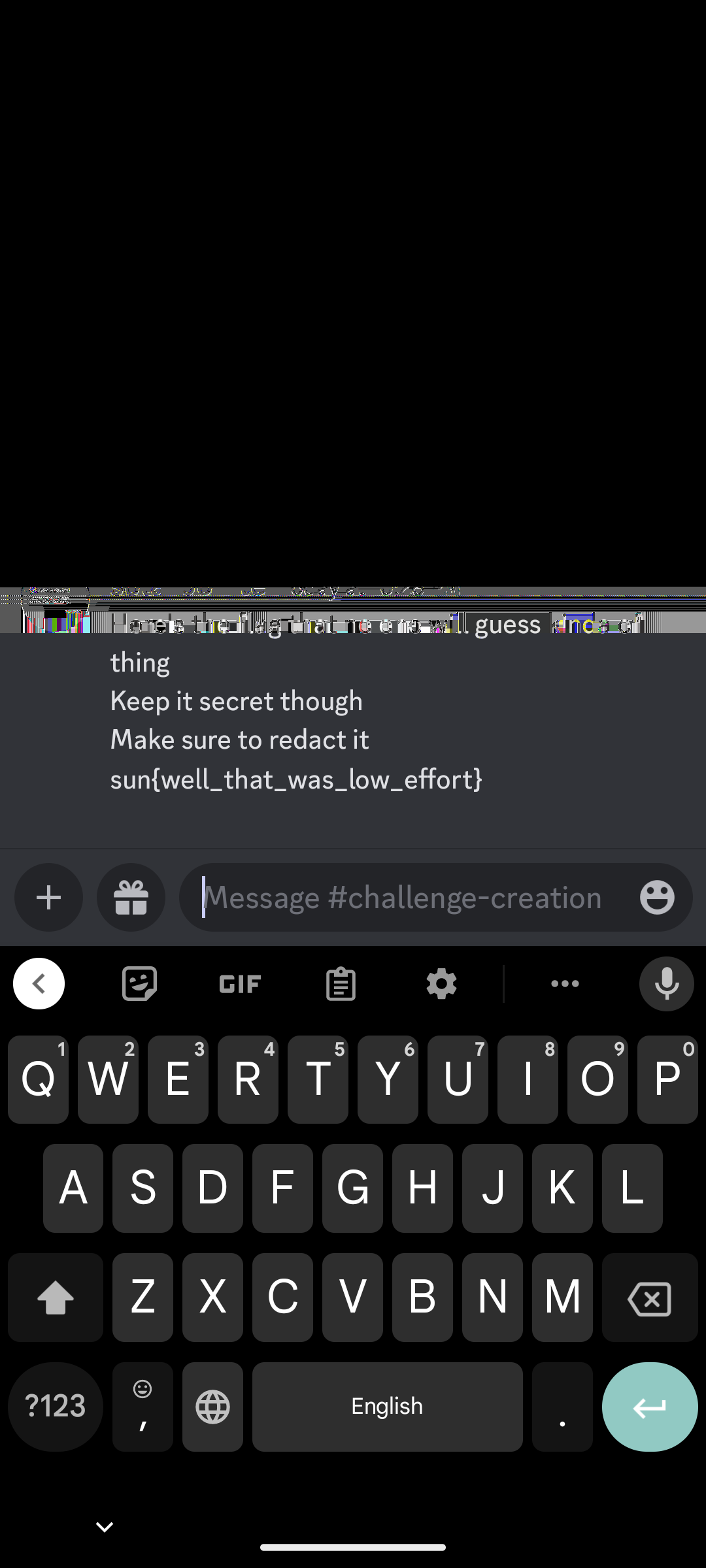
Now we have the flag: sun{well_that_was_low_effort}